Two-factor authentication (2FA), a type of multi-factor authentication (MFA), is a security process that cross-verifies users with two different forms of identification, most commonly knowledge of an email address and proof of ownership of a mobile phone.
Used on top of the regular username/password verification, 2FA bolsters security by making it more difficult for intruders to gain unauthorized access, even if a perpetrator gets past the first authentication step (e.g., brute forces a username and password).
Today, 2FA is commonly employed in online banking websites, social media platforms and e-commerce sites as a way to harden access controls to the more sensitive areas of a web application (e.g., admin panels or areas that store credit details and/or personal data).
Two-factor authentication also enables businesses and public institutions to be more productive and efficient, allowing employees to perform remote tasks with far less security concerns.
MFA identification can be categorized into three types:
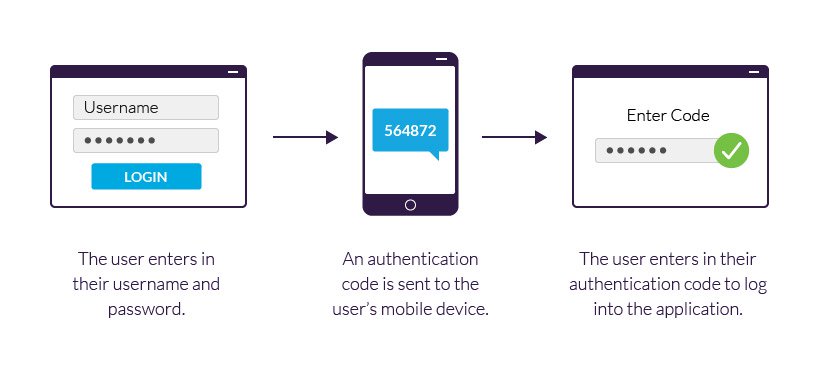
2FA example using a mobile device.
Typically, the 2FA method verifies the user’s identity against a knowledge factor alongside one of the remaining two factor types. Going to the ATM is a good example, as the bank requires that you provide both your credit card (possession factor) and your personal identification number (knowledge factor) to take out money.
2FA, and multi-factor authentication as a whole, is a reliable and effective system for blocking unauthorized access. It still, however, has some downsides. These include:
Two-factor authentication can play an important role in securing your website by blocking a number of application-based attacks.
These include brute force and dictionary attacks, in which perpetrators use automated software to generate massive amounts of username/password combinations in an attempt to guess a user’s credentials.
With 2FA enabled, these attacks are fruitless—even if perpetrators are able to discover a user’s password, they still lack the second form of identification needed to login to the application.
Additionally, two-factor authentication can help applications counter social engineering attacks, e.g., phishing and spear phishing, which attempt to dupe a user into revealing sensitive data, including their username and password. Even in the event of a successful attack, a perpetrator would still need the additional form of identification required by a 2FA solution.
As such, the Payment Card Industry (PCI) Data Security Standards (DSS), which is used to secure credit and debit card transactions against data theft and fraud, requires 2FA as a fundamental prerequisite for receiving certification.